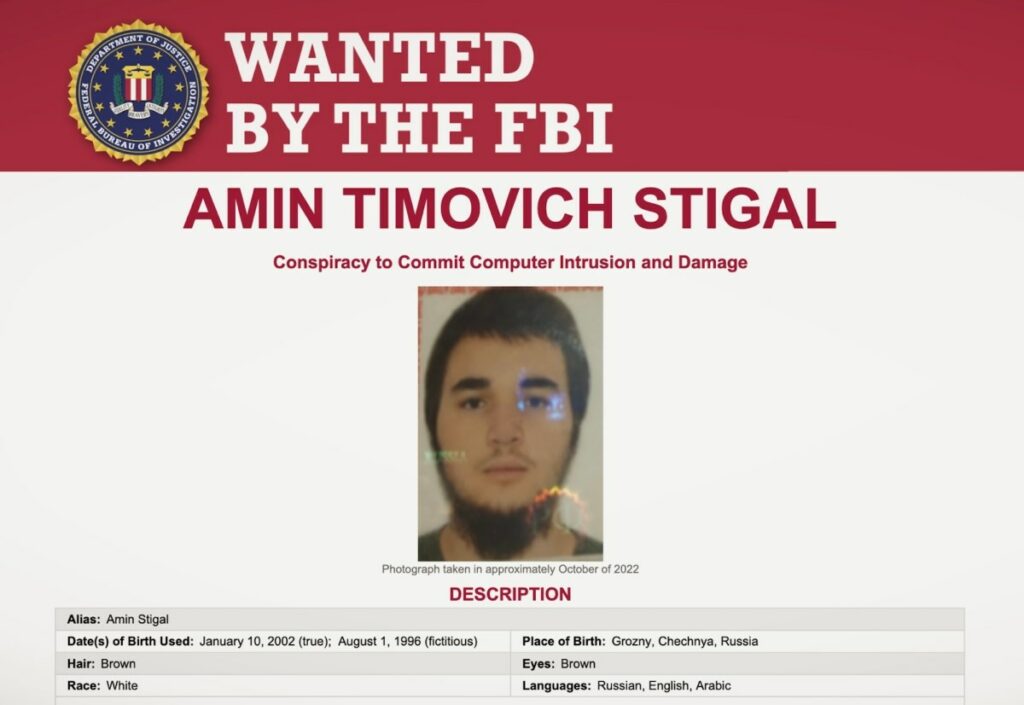
The Department of Justice has charged a Russian civilian with conspiracy to destroy Ukrainian government computer systems as part of a widespread hacking effort by Russia ahead of its illegal invasion of Ukraine.
U.S. prosecutors in Maryland said Wednesday that Amin Stigal, 22, is wanted for helping to set up servers used by Russian government hackers that were used to launch destructive cyberattacks on Ukraine government ministries in January 2022, a month before the Kremlin ordered tanks and troops to cross Ukraine’s borders.
The cyberattack campaign, known as “WhisperGate,” relied on so-called wiper malware that masqueraded as ransomware but deliberately and irreversibly scrambled the data on infected devices. Prosecutors said the cyberattacks were designed to “sow concern” among Ukrainian civil society about the safety of their government’s systems.
Stigal is also accused of helping the hackers working for Russia’s military intelligence unit — known as the GRU — to target allies of Ukraine, including the United States, according to the indictment against Stigal that was unsealed on Wednesday.
According to the unsealed indictment, Stigal allegedly used cryptocurrency to pay for and set up servers from an unnamed U.S.-based company, which allowed the Russian GRU hackers to launch their cyberattacks targeting the Ukrainian government with the data-destroying malware.
The Russian hackers stole reams of data during the cyberattacks, including citizens’ health data, criminal records and motor insurance data from Ukrainian government systems, the indictment alleges. The hackers later advertised the data for sale on known cybercrime forums.
U.S. prosecutors say the Russian hackers also targeted an unnamed U.S. government agency based in Maryland dozens of times between 2021 and 2022 prior to the invasion, allowing prosecutors in the district to take jurisdiction over the case and seek to charge Stigal.
Later in October 2022, the Russian hackers used the same servers set up by Stigal to target the transportation sector of one unnamed central European country, which U.S. prosecutors said delivered civilian and military aid to Ukraine following the invasion. The incident matches the timing of an October 2022 cyberattack in Denmark, which caused mass outages and delays across the country’s railway network at the time.
The U.S. government said it’s offering a $10 million bounty for information leading to the whereabouts or capture of Stigal, who remains at large and is believed to be in Russia.
Stigal faces up to five years in prison if convicted.